八嘎又拖队友后腿了……😭
Rev
晴窗细乳戏分茶
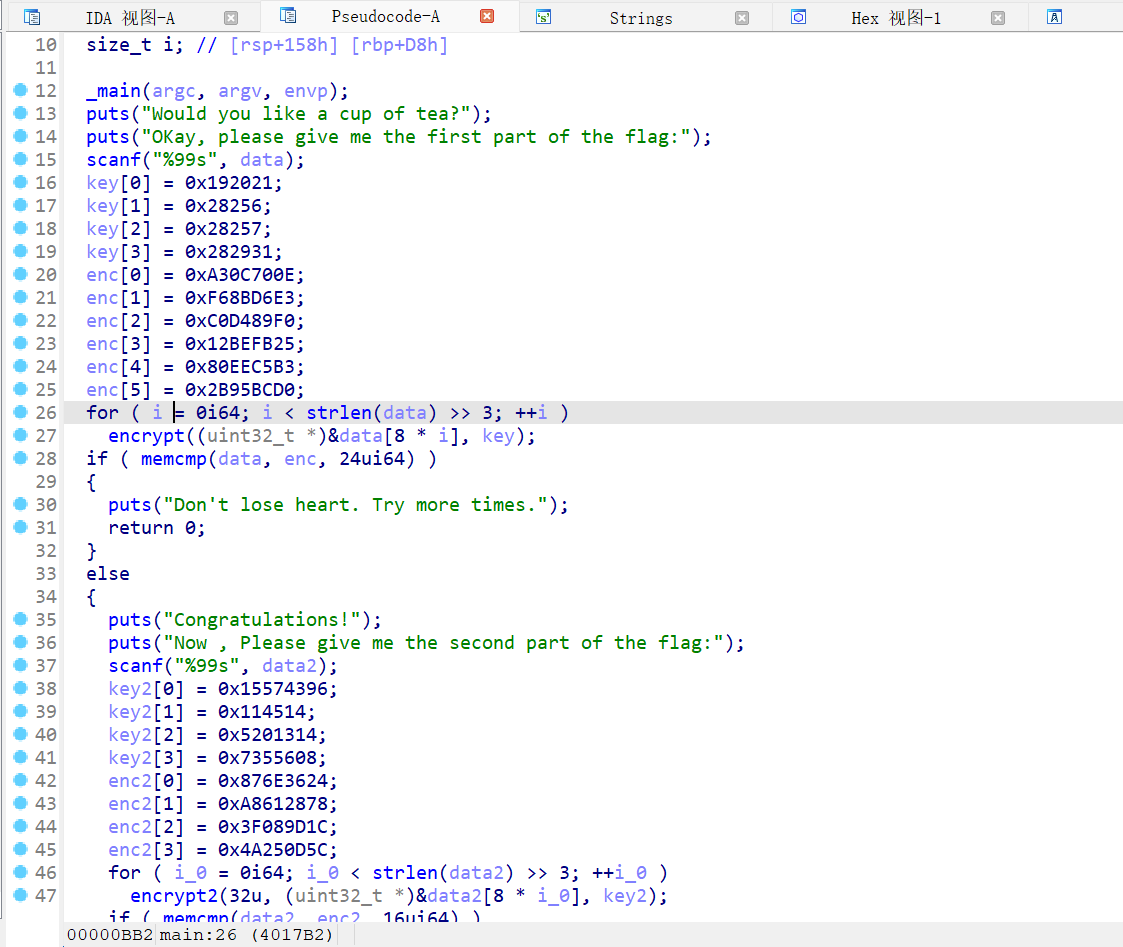
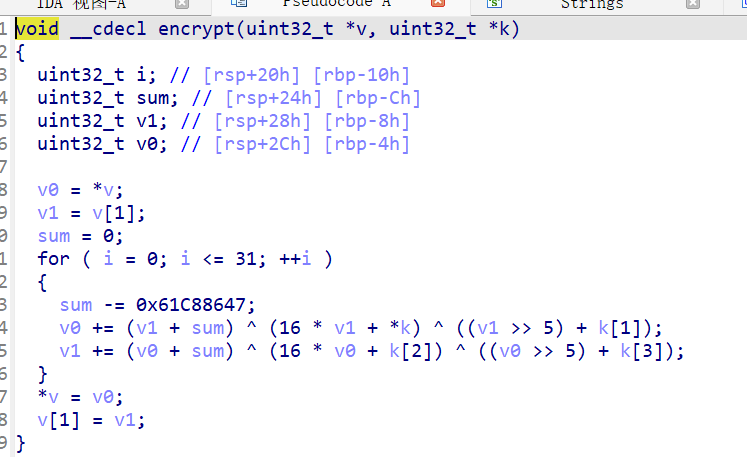
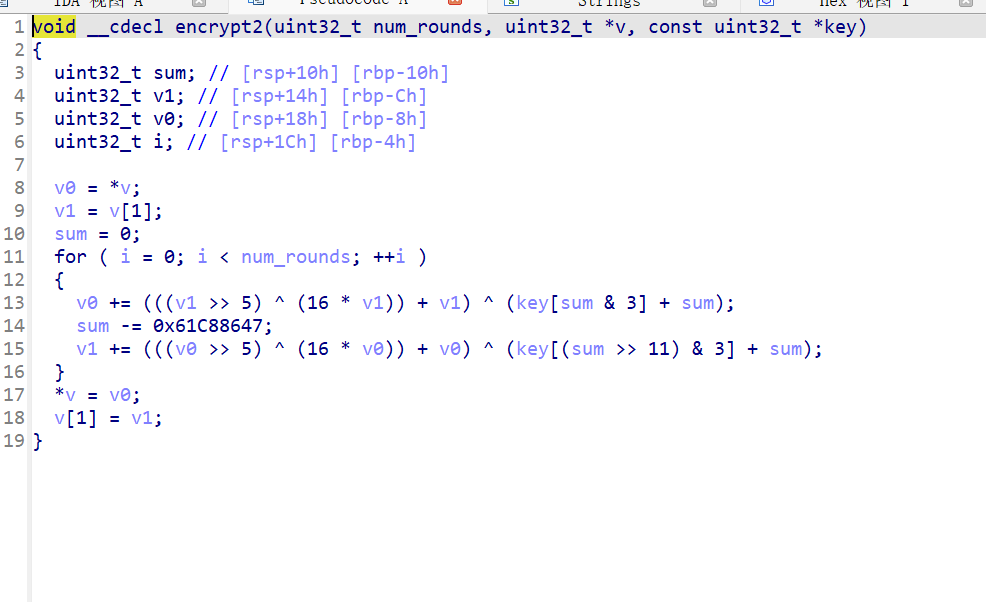
主函数内可见为分段加密,进入encrypt和encrypt2函数可确认第一段是标准TEA加密,第二段是标准XTEA加密
exp:
from ctypes import *
from Crypto.Util.number import *
def decrypt1(v,k):
v0=c_uint32(v[0])
v1=c_uint32(v[1])
delta=0x9e3779b9
sum=c_uint32(delta*32)
for i in range(32):
v1.value-=(v0.value+sum.value)^(v0.value*16+k[2])^((v0.value>>5)+k[3])
v0.value-=(v1.value+sum.value)^(v1.value*16+k[0])^((v1.value>>5)+k[1])
sum.value-=delta
print(v0.value,v1.value,end=",")
def decrypt2(v,k):
v0=c_uint32(v[0])
v1=c_uint32(v[1])
delta=0x9e3779b9
sum=c_uint32(delta*32)
for i in range(32):
v1.value-=(((v0.value>>5)^(v0.value*16))+v0.value)^(k[sum.value>>11&3]+sum.value)
v1.value=v1.value & 0xffffffff
sum.value-=delta
sum.value=sum.value & 0xffffffff
v0.value-=(((v1.value>>5)^(v1.value*16))+v1.value)^(k[sum.value&3]+sum.value)
# print(sum.value&3,(sum.value>>11)&3)
print(v0.value,v1.value,end=",")
if __name__=='__main__':
key=[0x192021,0x28256,0x28257,0x282931]
enc1=[0xA30C700E,0xF68BD6E3,0xC0D489F0,0x12BEFB25,0x80EEC5B3,0x2B95BCD0]
decrypt1(enc1[0:2],key)
decrypt1(enc1[2:4],key)
decrypt1(enc1[4:6],key)
key2=[0x15574396,0x114514,0x5201314,0x7355608]
enc2=[0x876e3624,0xa8612878,0x3f089d1c,0x4a250d5c]
decrypt2(enc2[0:2],key2)
decrypt2(enc2[2:4],key2)
soa=[1818850626,1179927396,1596998779,1601515641,1852388164,812867435,1415529837,2101297477]
for i in soa:
print(str(long_to_bytes(i)[::-1])[2:-1],end="")
自是花中第一流
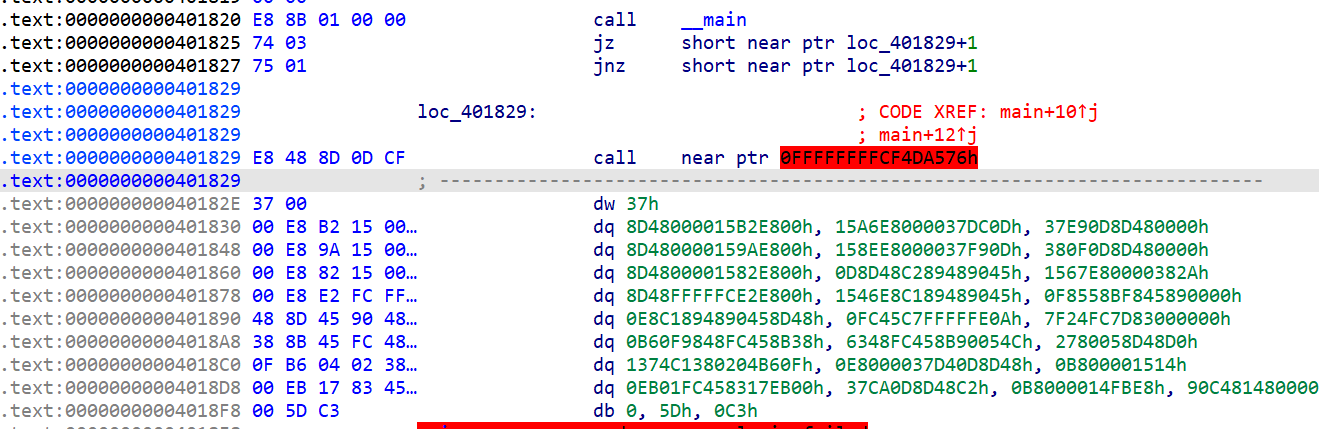
在主函数及init_key函数存在jz-jnz互补跳转
将junk code e8 nop掉即可F5
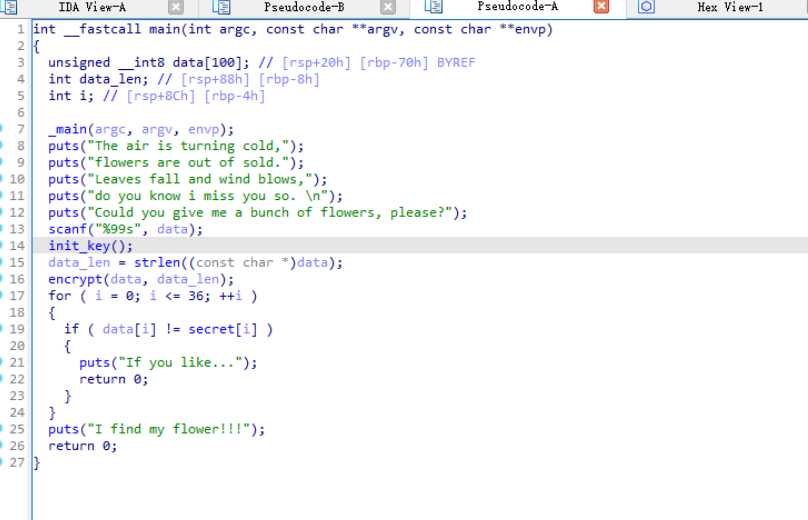
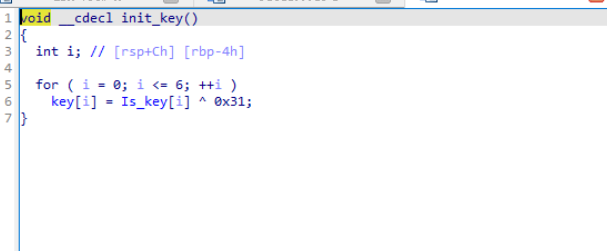
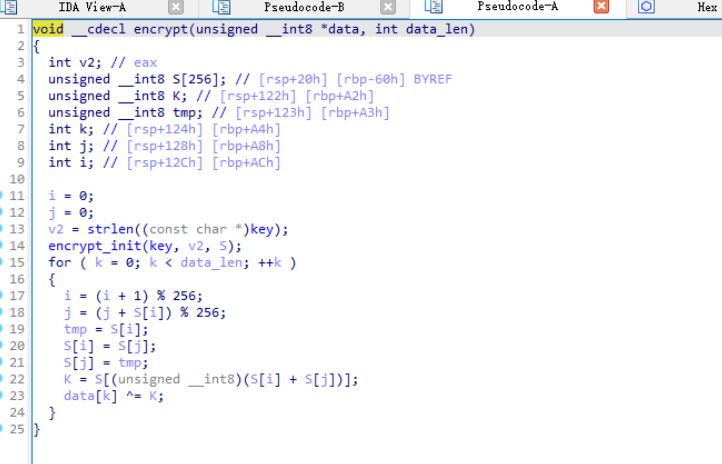
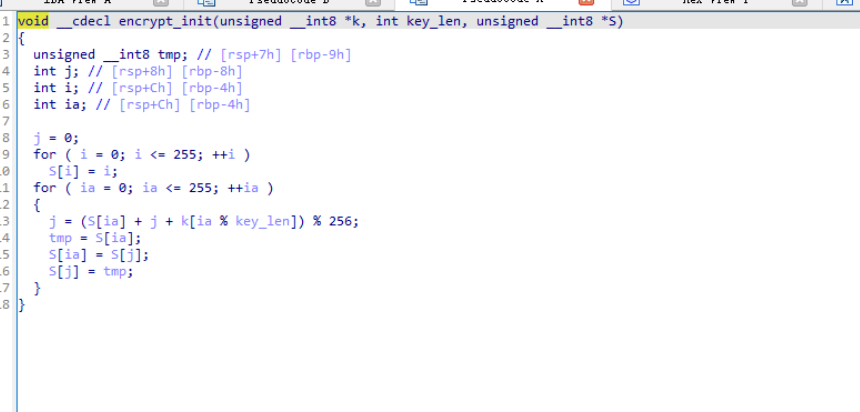
分析几个加密函数不难看出这是个标准RC4,key由Is_key异或0x31得到
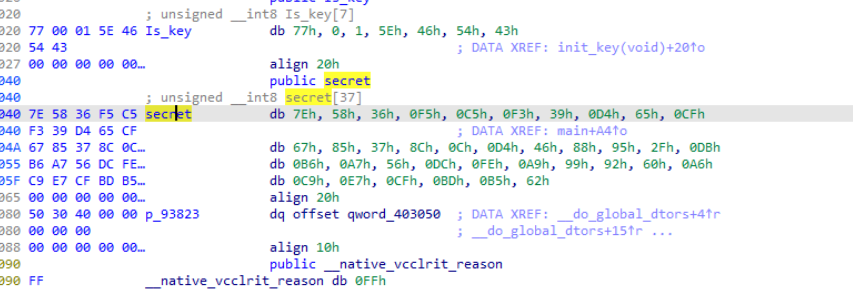
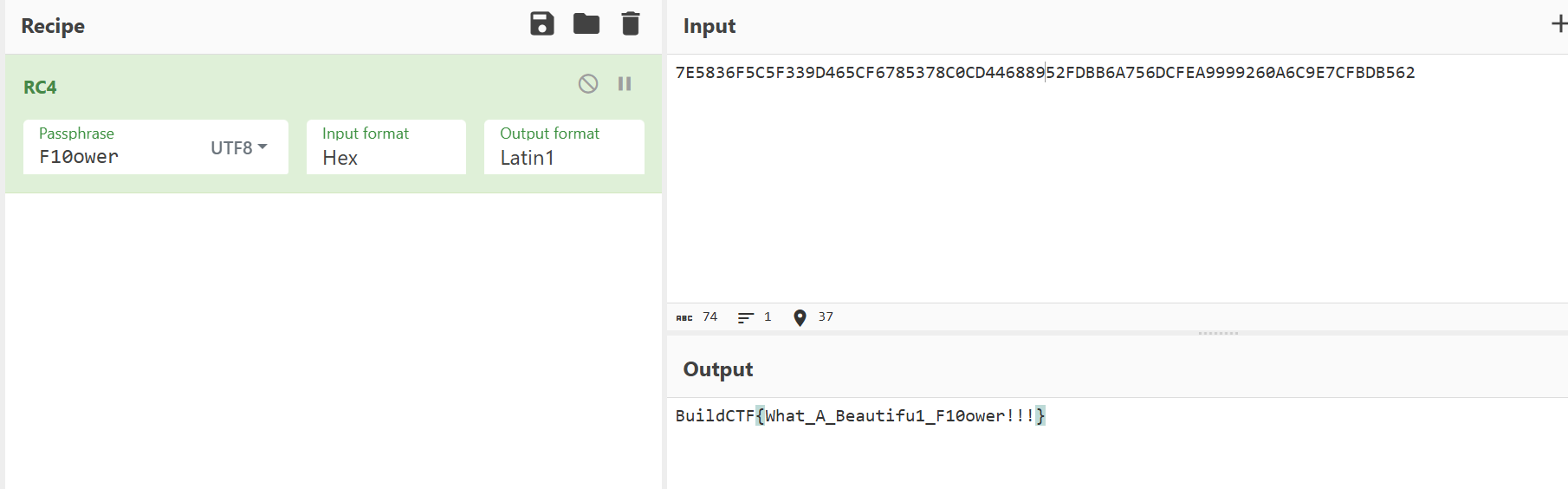
cyberchef解出即可
Babyre
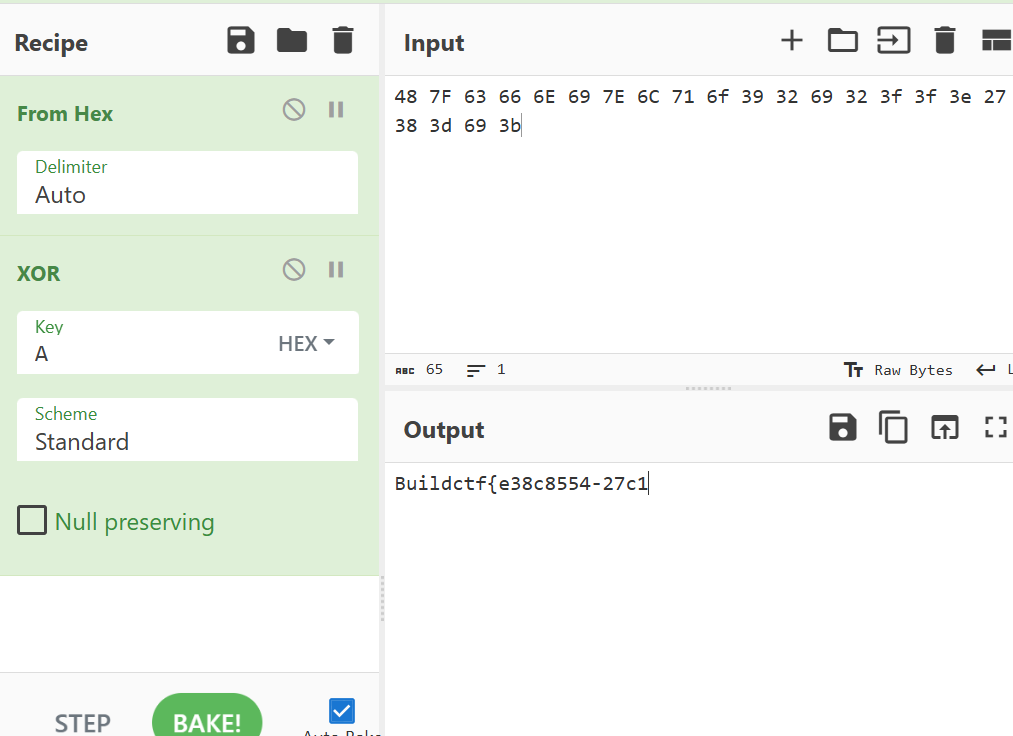
第一部分flag由简单异或0xA得到
Buildctf{e38c8554-27c1-4c2c-99ad-0a6d3ed66d1c}
小端序
第二部分密文
0x58,0x00,0x14,0x4E,0x51,0x51,0x57,0x19,0x56,0x57,0x52,0x57,0x51,0x1D,0x49,0x05,0x1E,0x52,0x55,0x52,0x00,0x52,0x01,0x56exp:
#include<stdio.h>
int main()
{
int enc[25]={0x19,0x57,0x51,0x51,0x4e ,0x14,0x00,0x58,0x05,0x49,0x1d,0x51,0x57,0x52,0x57,0x56,0x56,0x01,0x52,0x00,0x52,0x55,0x52,0x1e};
int key='-';
int tmp='}';
for(int i=0;i<=23;i++)
{
printf("%c,%x\n",enc[i]^key,enc[i]);
key^=enc[i];
}
printf("\n\n\n\n");
for(int i=23;i>=0;i--)
{
printf("%c,%x\n",enc[i]^tmp,enc[i]);
tmp^=enc[i];
}
}Ezmfc
下载附件,发现为MFC程序,无法使用IDA常规套路分析,于是尝试用Spy++和xspy查看窗口,但是并没有发现有用信息,于是尝试按照窗口显示提示操作
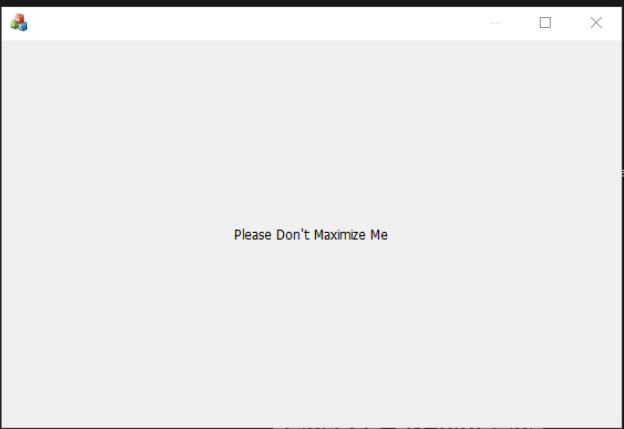
最大化后显示最小化即可获得flag,但最小化被ban掉了,猜测这里预期解应该要利用spy++修改窗口属性,但是可以通过任务管理器直接最小化窗口
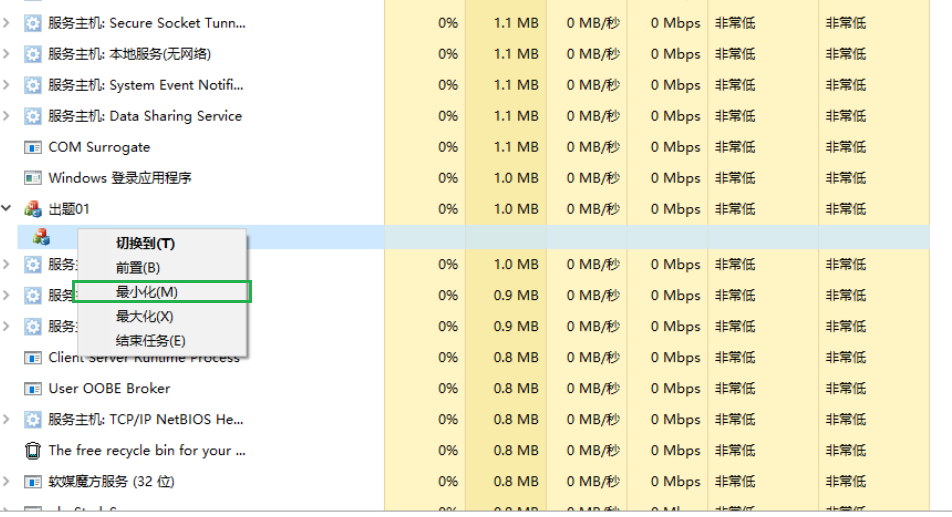
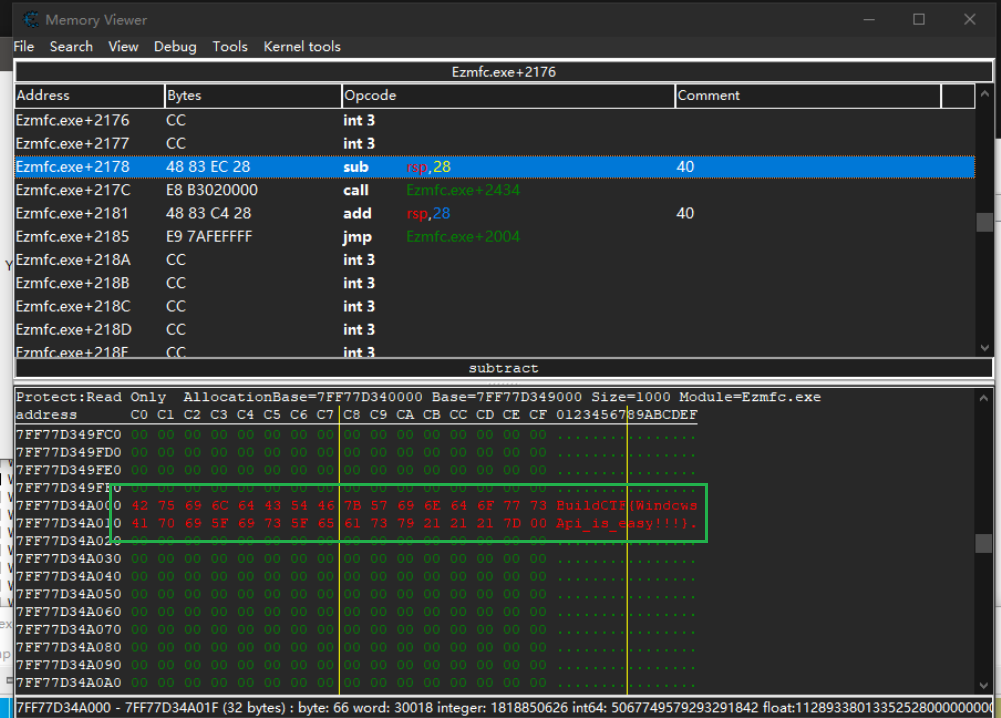
随后根据最小化之后的窗口提示,使用CE查看内存即可获得flag
pyc
使用在线工具反编译pyc
exp:
import base64
def decode(enc):
enc1=base64.b64decode(bytes(enc)).decode('utf-8')
s=bytearray()
for i in enc1:
if i > 255:
i+=256
i-=16
i=ord(i)^32
print(enc1)
if __name__ = '__main__':
enc="cmVZXFRzhHZrYFNpjyFjj1VRVWmPVl9ij4kgZW0="
decode(enc)
ez_xor
进入主函数,整理一下符号,不难发现v9数组为密文,encrypt函数为加密函数,密钥为aBuildctf2024
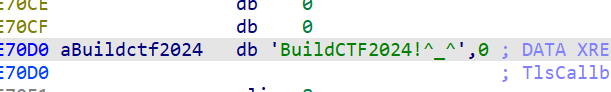
encrypt函数内的逻辑很简单,先将key传入key_init函数生成长度为256的密码盒,然后再用密码盒对明文进行加密
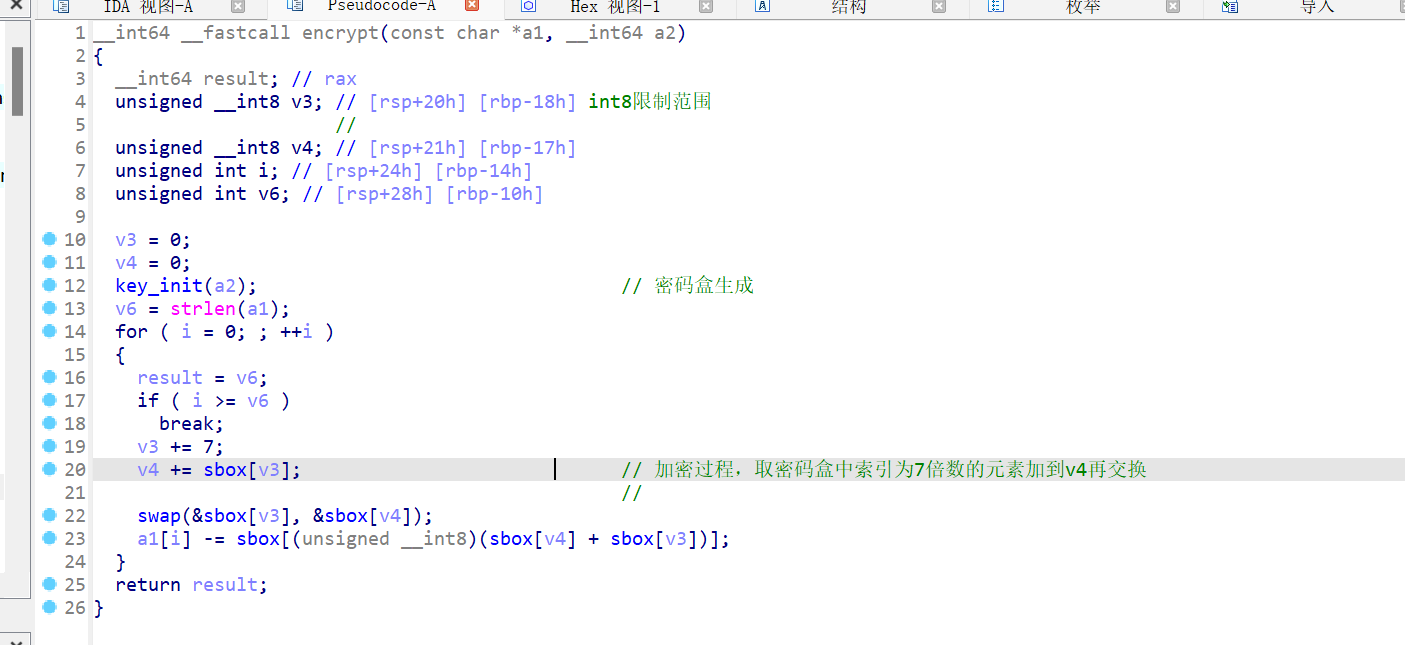
那么只需要获取密码盒子后逆序解密即可,动调之
exp
#include<stdio.h>
#include<stdlib.h>
#include<string.h>
#include <Windows.h>
char sbox[256] = {
0xF7, 0xA0, 0xD3, 0xD5, 0xB6, 0xE2, 0x6B, 0x8F, 0xCB, 0x33,
0xA8, 0x30, 0x21, 0xEA, 0x4D, 0x7F, 0xCF, 0x69, 0x1C, 0x50,
0x84, 0x1A, 0xB8, 0x78, 0xD6, 0x72, 0xDF, 0x20, 0xFA, 0x2E,
0xBD, 0x87, 0x43, 0xCC, 0xE9, 0xBC, 0x35, 0xD8, 0x0A, 0x8A,
0xDA, 0x2C, 0xDE, 0xF1, 0x5F, 0xE6, 0xAB, 0x4C, 0xE7, 0x12,
0x41, 0x14, 0x7B, 0x46, 0x4B, 0xEE, 0x03, 0x79, 0xF3, 0xAC,
0xB9, 0x07, 0x34, 0x17, 0x96, 0x51, 0xCE, 0x0B, 0x16, 0x9E,
0xB1, 0x58, 0x8C, 0x27, 0xC5, 0x3D, 0x6D, 0xA6, 0xC1, 0x42,
0x48, 0x63, 0x9F, 0x70, 0x9B, 0x09, 0x77, 0x00, 0x9C, 0xC0,
0x38, 0xC6, 0x5D, 0xBA, 0x53, 0x66, 0xDC, 0x57, 0xF5, 0x1E,
0x0D, 0x76, 0x98, 0x22, 0x62, 0x89, 0xA7, 0x52, 0xFE, 0xFF,
0xA9, 0x95, 0x71, 0x2D, 0x59, 0x4E, 0x5B, 0xA1, 0xF8, 0xE1,
0xE4, 0x11, 0x93, 0xBE, 0x1D, 0x19, 0x80, 0x7C, 0x32, 0x25,
0x31, 0x83, 0x44, 0xBB, 0x64, 0xA2, 0x18, 0x6E, 0x1F, 0x7D,
0xA4, 0x65, 0xFD, 0xCD, 0xC2, 0xF2, 0x10, 0xE3, 0x61, 0x9A,
0xD1, 0x3E, 0x47, 0x39, 0x24, 0x2F, 0xB7, 0x54, 0x15, 0xDD,
0xA5, 0xBF, 0xEB, 0xB0, 0x56, 0xFC, 0x05, 0x60, 0xEC, 0x81,
0xE8, 0xAE, 0x55, 0x6C, 0x99, 0x4F, 0x26, 0x3C, 0xF0, 0xB2,
0xD7, 0xAF, 0xD0, 0xD2, 0x01, 0x4A, 0xD4, 0x29, 0x45, 0xCA,
0x23, 0xC8, 0xB5, 0x0F, 0x5A, 0x2A, 0x2B, 0xDB, 0x1B, 0xAD,
0x0E, 0x8D, 0x28, 0x3A, 0x74, 0x7A, 0x08, 0xC3, 0x6A, 0x88,
0xA3, 0x90, 0xF6, 0x49, 0x5E, 0xF9, 0x8E, 0x9D, 0xB4, 0xEF,
0xB3, 0x97, 0xC7, 0x02, 0xE5, 0x94, 0x73, 0x68, 0x06, 0x3B,
0x40, 0x85, 0x8B, 0x67, 0x75, 0x6F, 0x7E, 0x13, 0xAA, 0xED,
0xFB, 0x04, 0x91, 0x86, 0x3F, 0x36, 0x5C, 0x82, 0x0C, 0xC9,
0xC4, 0x37, 0xD9, 0x92, 0xF4, 0xE0 };
char* __fastcall swap(char* a1,char* a2)
{
char* result; // rax
char v3; // [rsp+0h] [rbp-18h]
v3 = *a1;
*a1 = *a2;
result = a2;
*a2 = v3;
return result;
}
//__int64 __fastcall initialize_key(char* a1)
//{
// __int64 result; // rax
// int k; // [rsp+20h] [rbp-138h]
// unsigned int i; // [rsp+24h] [rbp-134h]
// int j; // [rsp+28h] [rbp-130h]
// int v5; // [rsp+2Ch] [rbp-12Ch]
// unsigned int v6; // [rsp+30h] [rbp-128h]
// char v7[256]; // [rsp+40h] [rbp-118h] BYREF
//
// for (i = 0; i < 256; ++i)
// sbox[i] = i;
// v6 = 31;
// result = 0i64;
// memset(v7, 0, sizeof(v7));
// for (j = 0; j < 256; ++j)
// {
// v7[j] = a1[j % v6];
// result = (unsigned int)(j + 1);
// }
// v5 = 0;
// for (k = 0; k < 256; ++k)
// {
// v5 = ((unsigned __int8)v7[k] + (unsigned __int8)sbox[k] % 63 + v5) % 256;
// swap(&sbox[k], &sbox[v5]);
// result = (unsigned int)(k + 1);
// }
// for (int i = 0;i <= 255;i++)
// {
// printf("0x%x,", sbox[i]);
// }
// return result;
//}
//__int64 __fastcall encrypt(char* a1,char* a2)
//{
// __int64 result; // rax
// unsigned __int8 v3; // [rsp+20h] [rbp-18h]
// unsigned __int8 v4; // [rsp+21h] [rbp-17h]
// unsigned int i; // [rsp+24h] [rbp-14h]
// unsigned int v6; // [rsp+28h] [rbp-10h]
// v3 = 0;
// v4 = 0;
// initialize_key(a2);
// v6 = 31;
// for (i = 0; i<31; ++i)
// {
// result = v6;
// v3 += 7;
// v4 += sbox[v3];
// swap((char* ) & sbox[v3],(char* ) & sbox[v4]);
// //printf("v34=%x %x\n", v3, v4);
// a1[i] -= sbox[(unsigned __int8)(sbox[v4] + sbox[v3])];
//
// }
// return result;
//}
__int64 __fastcall decrypt(char* a1)
{
_int64 result; // rax
unsigned __int8 v3 = 0xe0;// [rsp+20h] [rbp-18h]
unsigned __int8 v4 = 0xcf; // [rsp+21h] [rbp-17h]
int i; // [rsp+24h] [rbp-14h]
unsigned int v6; // [rsp+28h] [rbp-10h]
v6 = strlen(a1);
for (i = 31;i >= 0; i--) {
a1[i] += sbox[(unsigned __int8)(sbox[v4] + sbox[v3])];
swap((char*)&sbox[v3], (char*)&sbox[v4]);
v4 -= sbox[v3];
v3 -= 7;
result = v6;
}
return result;
}
int main()
{
unsigned char key[17] = "BuildCTF2024!^_^";
unsigned char C[32] = "1234567891234567891234567891234";
unsigned char enc[]= { 0x19,0x68,0xA2,0xEF,0x7B,0xBA,0x0E,0xC5,0x5D,0x80,0xEF,0x09,0x0B,0xD1,0x81,0xF1,0xF0,0x33,0xA6,0x11,0x23,0x58,0x5C,0x2B,0x38,0x8D,0x80,0x61,0x27,0x48,0x35,0x00 };
/*encrypt((char*)C,(char*)key);*/
decrypt((char*)enc);
for (int i = 0;i <= 31;i++)
printf("%x ", enc[i]);
// initialize_key((char*)key);
}