Rev[week1 AK]
Binary Master
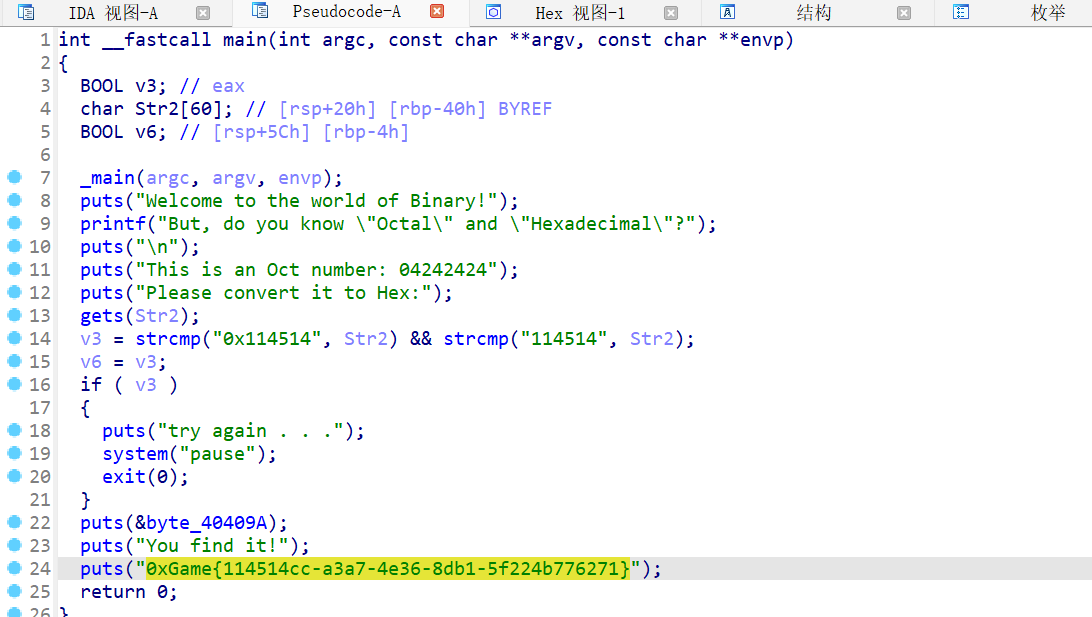
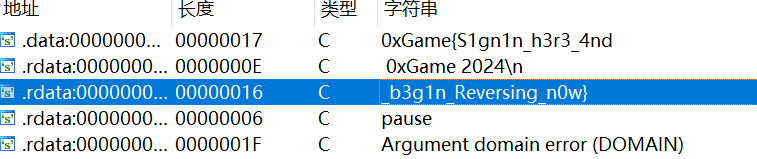
IDA喵了
解法二:
理论上输入0x114514也行
signsign
Babybase
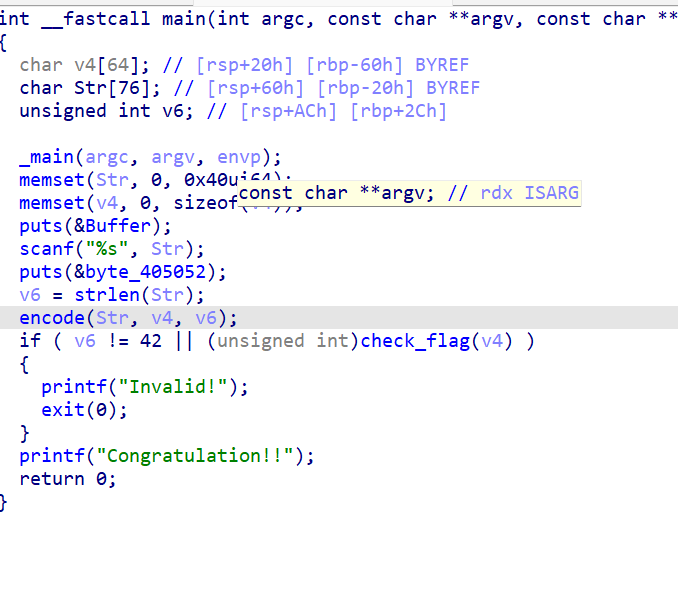
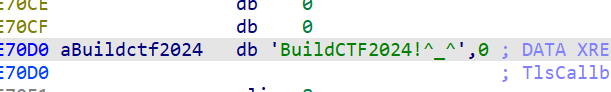
Str为输入字符串,v4为加密后字符串,在checkflag内与
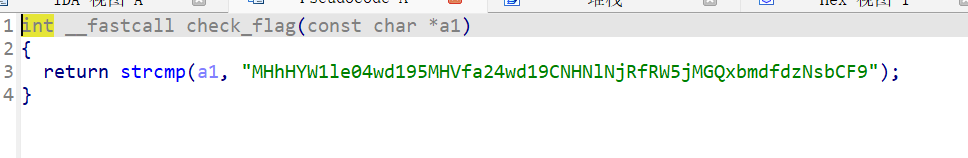
比较,回到encode函数
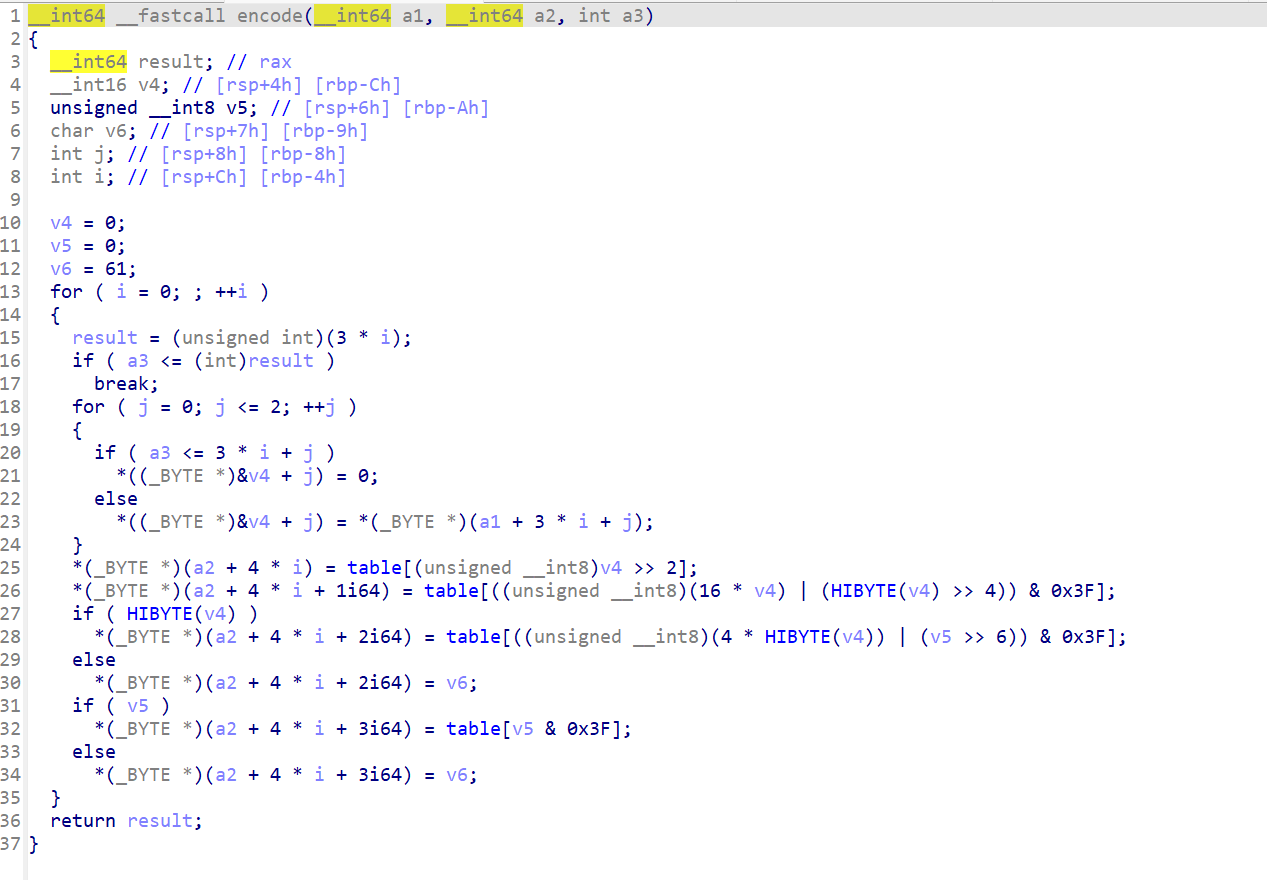
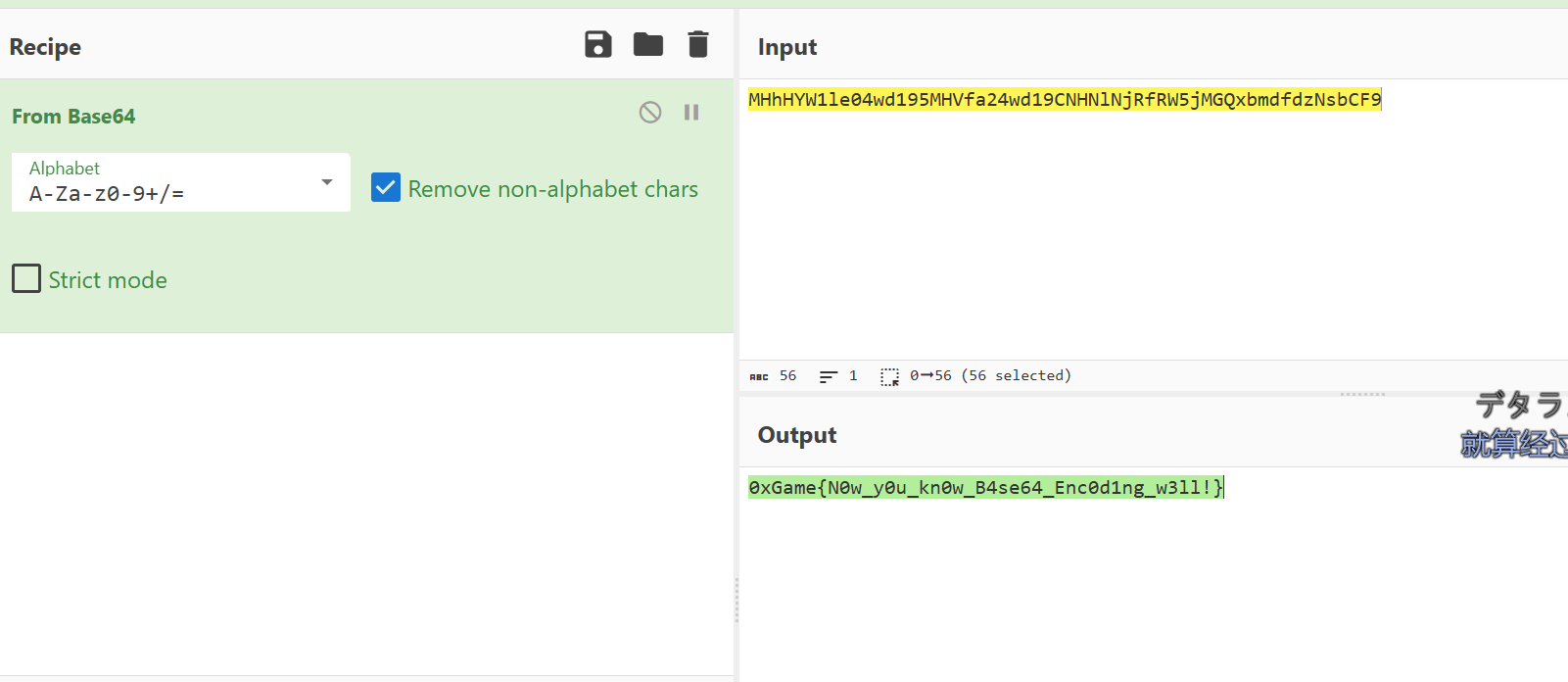
不难发现这是个标准base64
xor_beginning
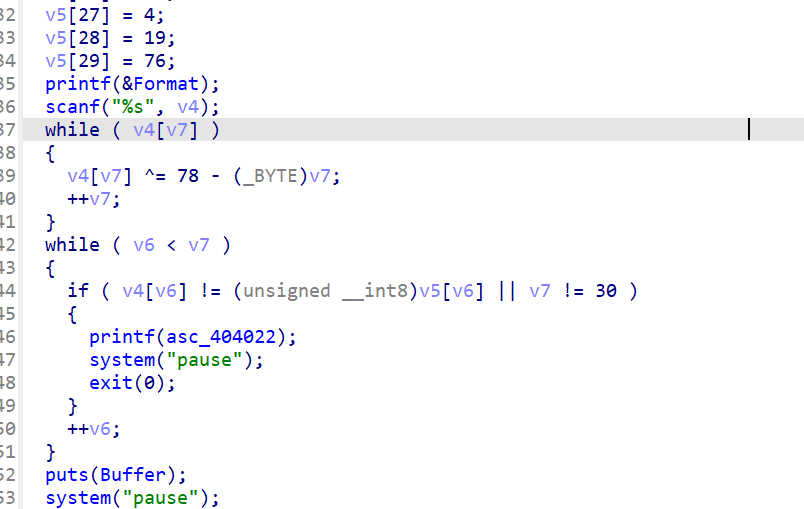
密文在v5内,异或78-i
exp:
#include<bits/stdc++.h>
int main()
{
char v5[40];
strcpy(v5, "~5\v*',3");
v5[7] = 31;
v5[8] = 118;
v5[9] = 55;
v5[10] = 27;
v5[11] = 114;
v5[12] = 49;
v5[13] = 30;
v5[14] = 54;
v5[15] = 12;
v5[16] = 76;
v5[17] = 68;
v5[18] = 99;
v5[19] = 114;
v5[20] = 87;
v5[21] = 73;
v5[22] = 8;
v5[23] = 69;
v5[24] = 66;
v5[25] = 1;
v5[26] = 90;
v5[27] = 4;
v5[28] = 19;
v5[29] = 76;
for(int i=0;i<=29;i++)
{
printf("%c",v5[i]^78-i);
}
return 0;
} xor_Endian
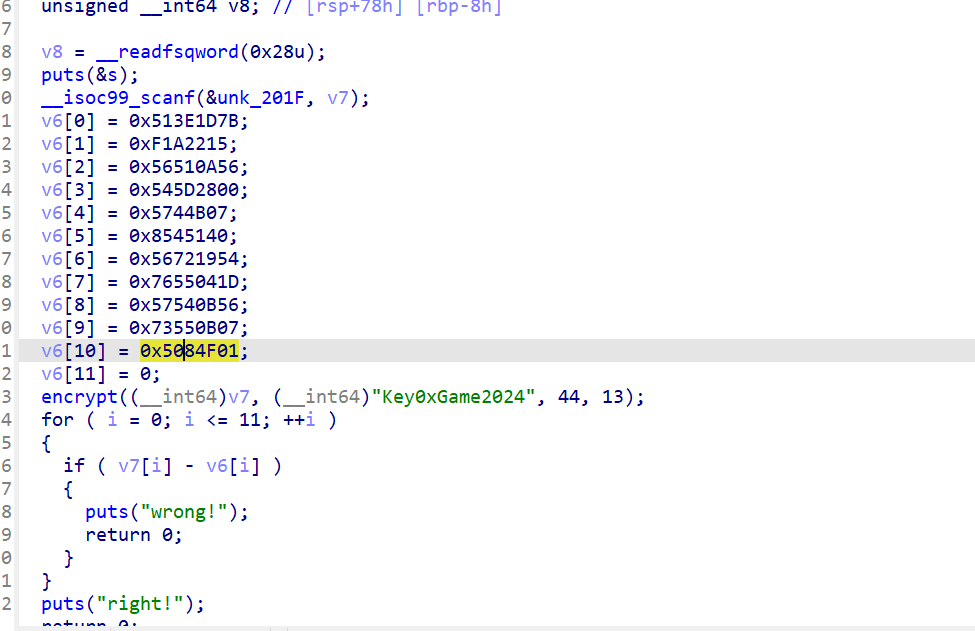
v6为密文,encrypt函数:
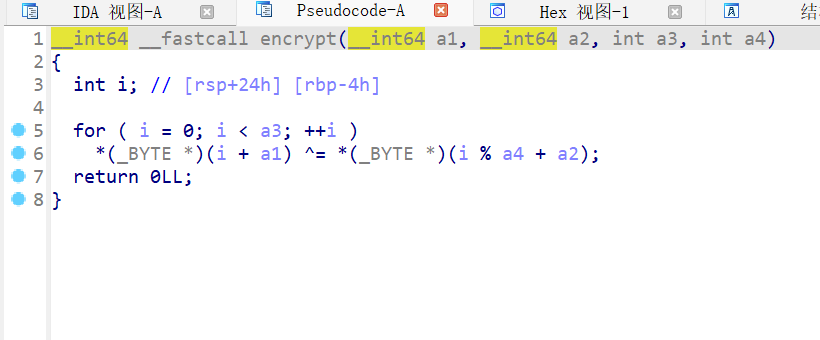
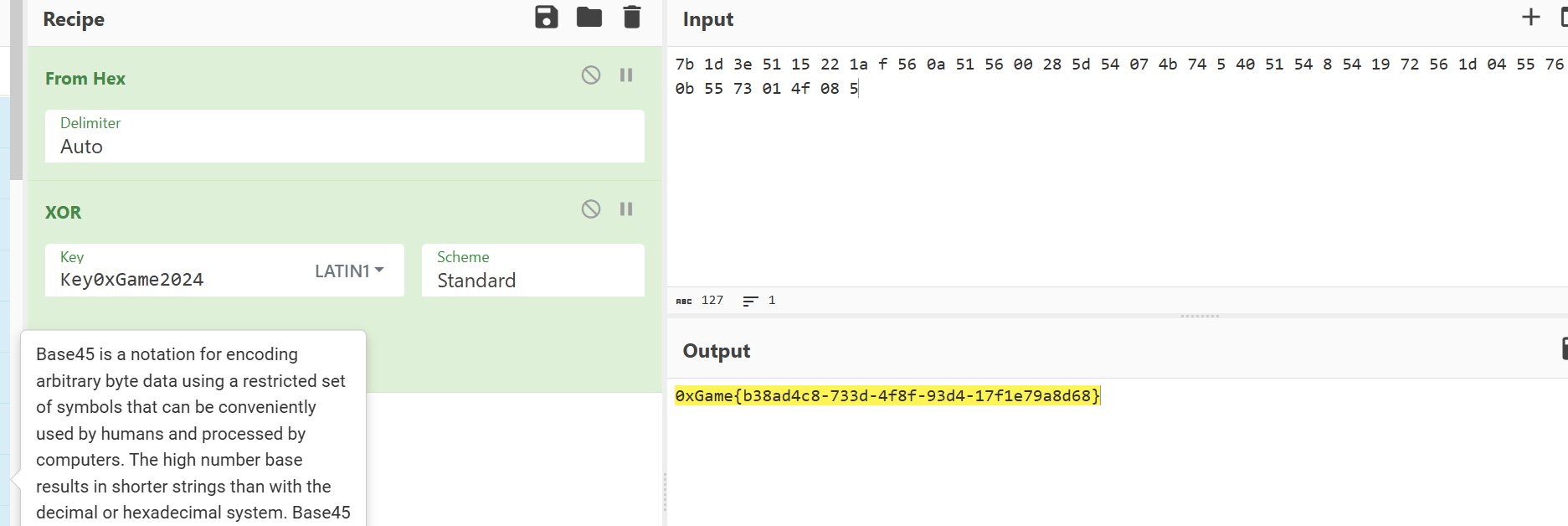
以Key0xGame2024为密钥依次异或,结合题目所述Endian,小端序排列密文解密即可
[W2]BabyUPX
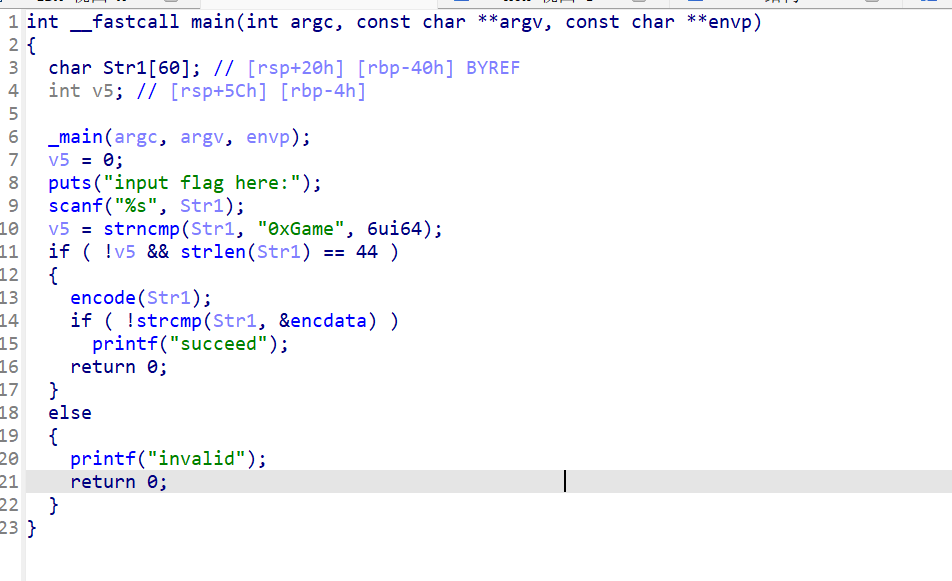
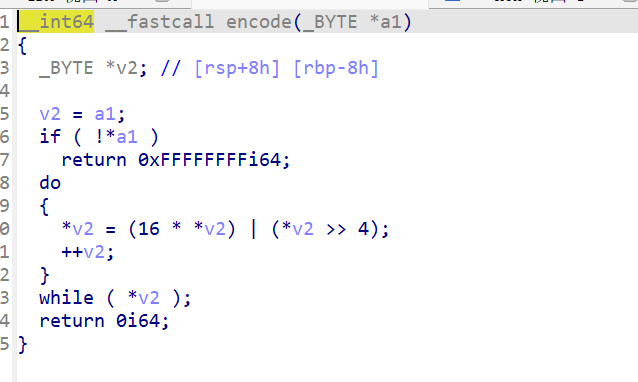
加密方式为交换高低四位
exp
#include<bits/stdc++.h>
int main()
{
int enc[44]={0x03, 0x87, 0x74, 0x16, 0xD6, 0x56, 0xB7, 0x63, 0x83, 0x46, 0x66, 0x66, 0x43, 0x53, 0x83, 0xD2,
0x23, 0x93, 0x56, 0x53, 0xD2, 0x43, 0x36, 0x36, 0x03, 0xD2, 0x16, 0x93, 0x36, 0x26, 0xD2, 0x93,
0x73, 0x13, 0x66, 0x56, 0x36, 0x33, 0x33, 0x83, 0x56, 0x23, 0x66};
for(int i=0;i<=43;i++)
{
printf("%c",(((enc[i]&0x0f)<<4)|((enc[i]&0xf0)>>4)));
}
return 0;
} 0xGame{68dff458-29e5-4cc0-a9cb-971fec338e2f}EzPyc
import hashlib
user_input = input('请输入神秘代号:')
if user_input != 'Ciallo~':
print('代号不是这个哦')
exit()
input_hash = hashlib.md5(user_input.encode()).hexdigest()
input_hash = list(input_hash)
for i in range(len(input_hash)):
if ord(input_hash[i]) in range(48, 58):
original_num = int(input_hash[i])
new_num = (original_num + 5) % 10
input_hash[i] = str(new_num)
input_hash = ''.join(input_hash)
print('0xGame{{{}}}'.format(input_hash))md5:7f5ef5762bf8a2c043d836b522127e54
exp:
fakeflag='7f5ef5762bf8a2c043d836b522127e54'
fakeflag=list(fakeflag)
for i in range(len(fakeflag)):
if ord(fakeflag[i]) in range(48, 58):
original_num = int(fakeflag[i])
new_num = (original_num + 5) % 10
fakeflag[i] = str(new_num)
print(fakeflag)
# //2f0ef0217bf3a7c598d381b077672e09EzJar
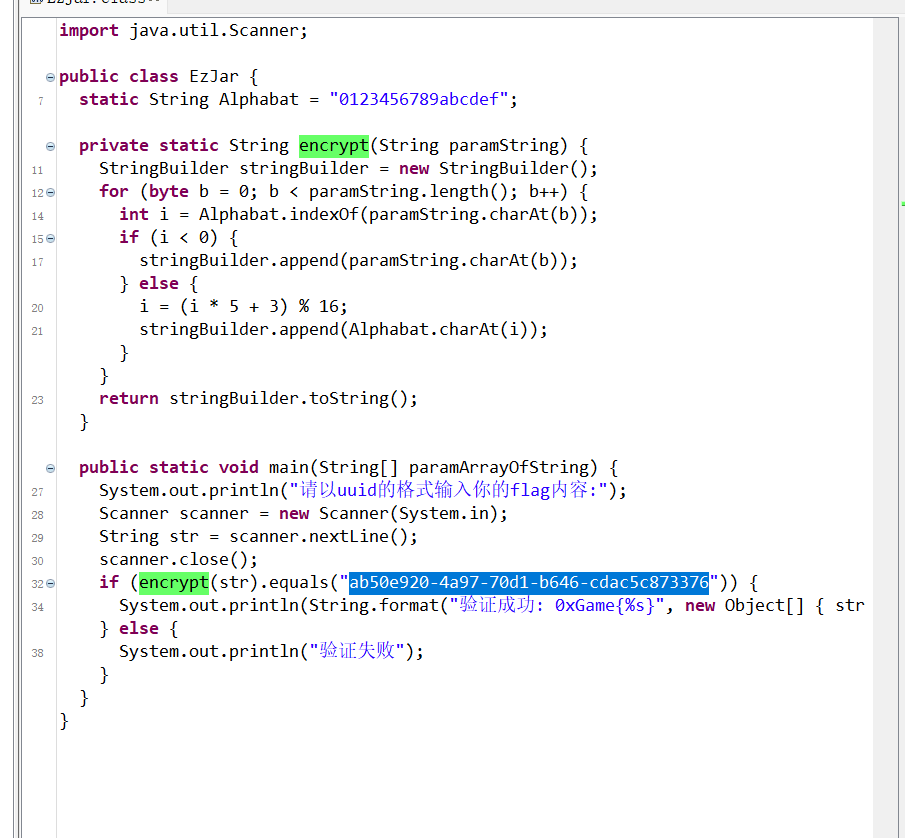
def find_multiplicative_inverse(a, m):
for x in range(1, m):
if (a * x) % m == 1:
return x
return None
def decrypt(ciphertext):
Alphabat = "0123456789abcdef"
decrypted_string = ""
# Find the multiplicative inverse of 5 modulo 16
inverse = find_multiplicative_inverse(5, 16)
for char in ciphertext:
if char in Alphabat:
# Find the index of the character in Alphabat
i = Alphabat.index(char)
# Reverse the transformation using the multiplicative inverse
original_index = (i - 3 + 16) % 16 # Adding 16 to ensure non-negative result
original_index = (original_index * inverse) % 16
decrypted_string += Alphabat[original_index]
else:
decrypted_string += char
return decrypted_string
# Given ciphertext
ciphertext = "ab50e920-4a97-70d1-b646-cdac5c873376"
# Decrypt the ciphertext
decrypted_text = decrypt(ciphertext)
print(decrypted_text)
ZZZ
v10: 842086455 v11: 862073908 v12: 1681208161 v13: 3846448765 v14: 229272473174436
0xGame{e544267d-842086455-862073908-1681208161-d085a85201a4}
Pwn
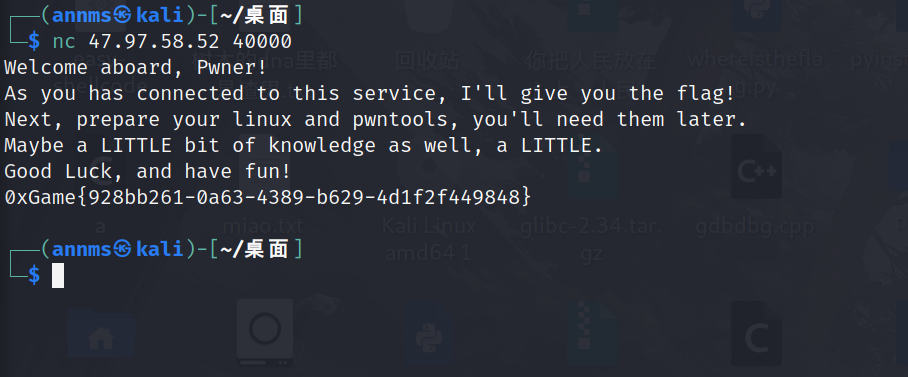
0.test your nc
Crypto
Caesar Cipher
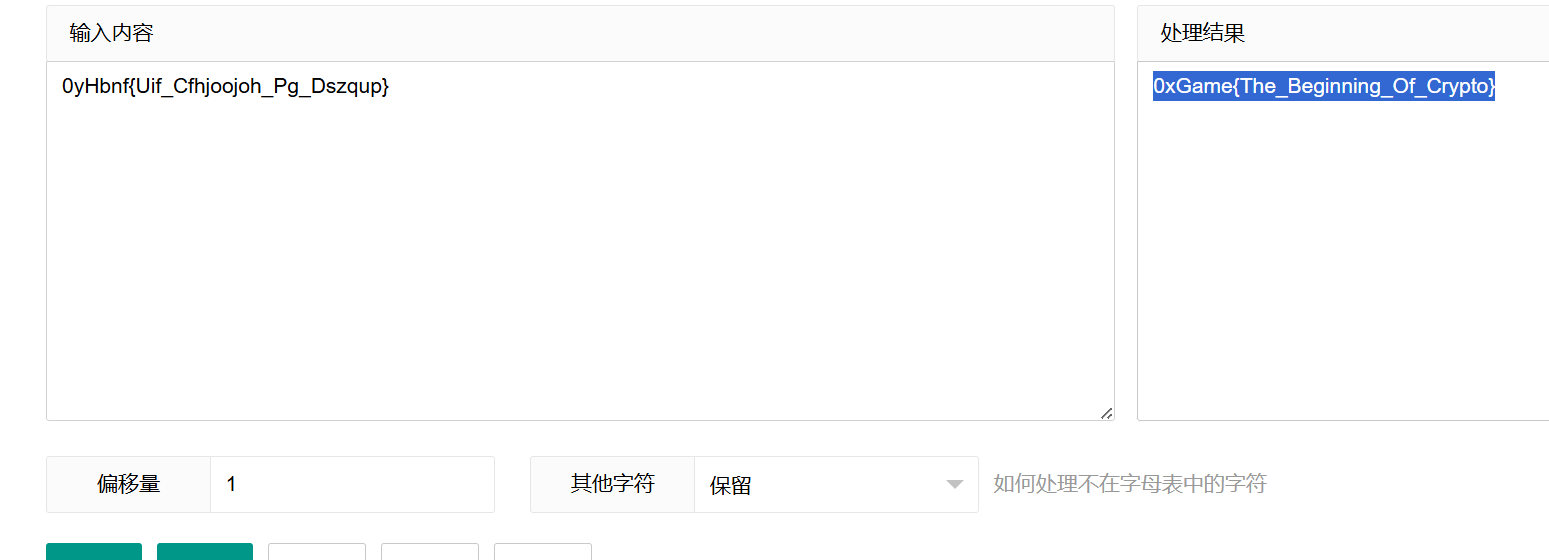
根据第二位可知偏移量为1