Annms_
begin
IDA教程题,跟着提示一步步走即可
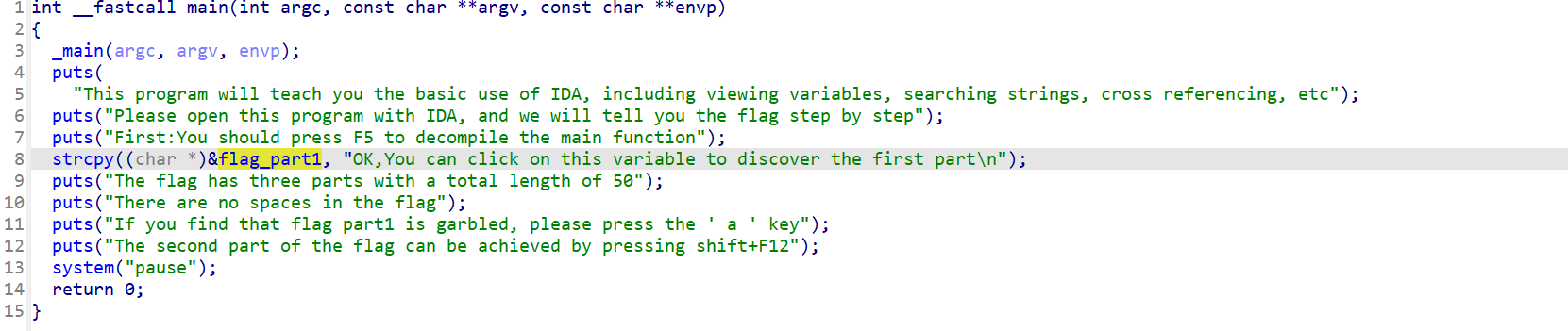
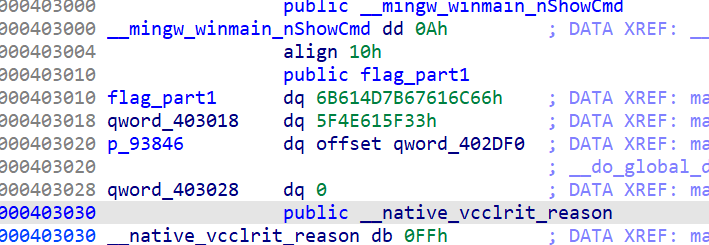

flag{Mak3_aN_
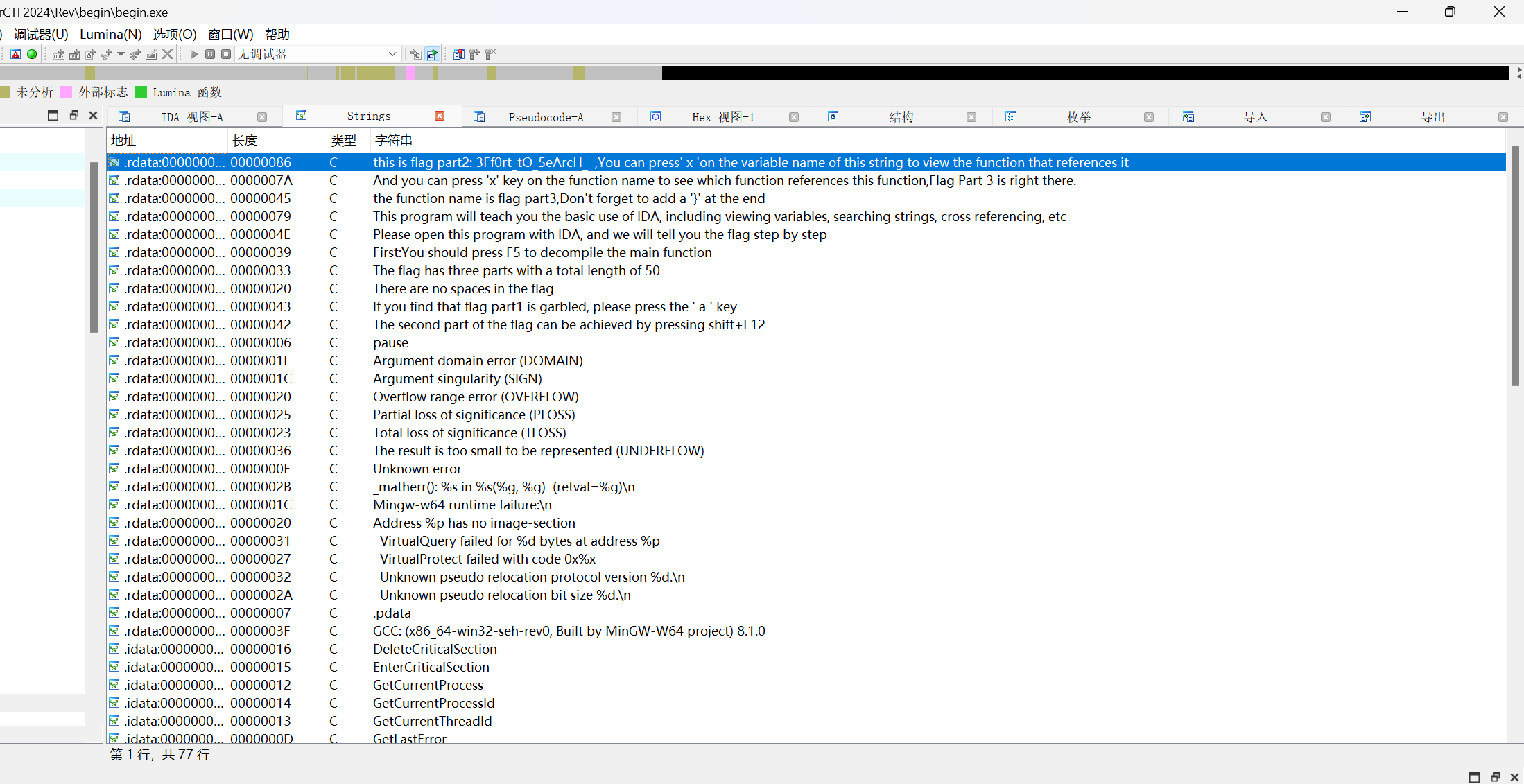
3Ff0rt_tO_5eArcH_
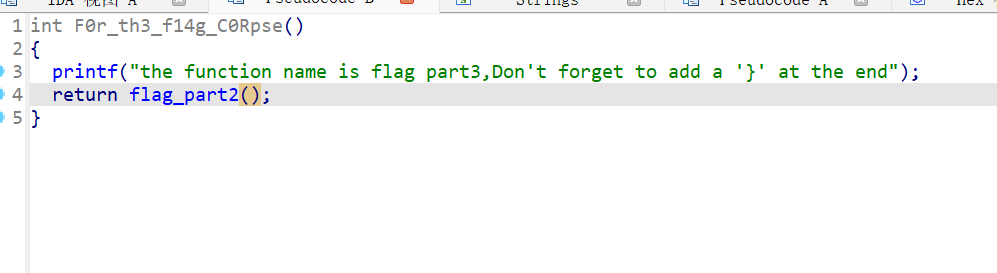
F0r_th3_f14g_C0Rpse
flag{Mak3_aN_3Ff0rt_tO_5eArcH_F0r_th3_f14g_C0Rpse}
base64
根据题目提示和加密函数可判断出这是换表base64,在字符串页面可以找到密文及编码表
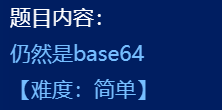
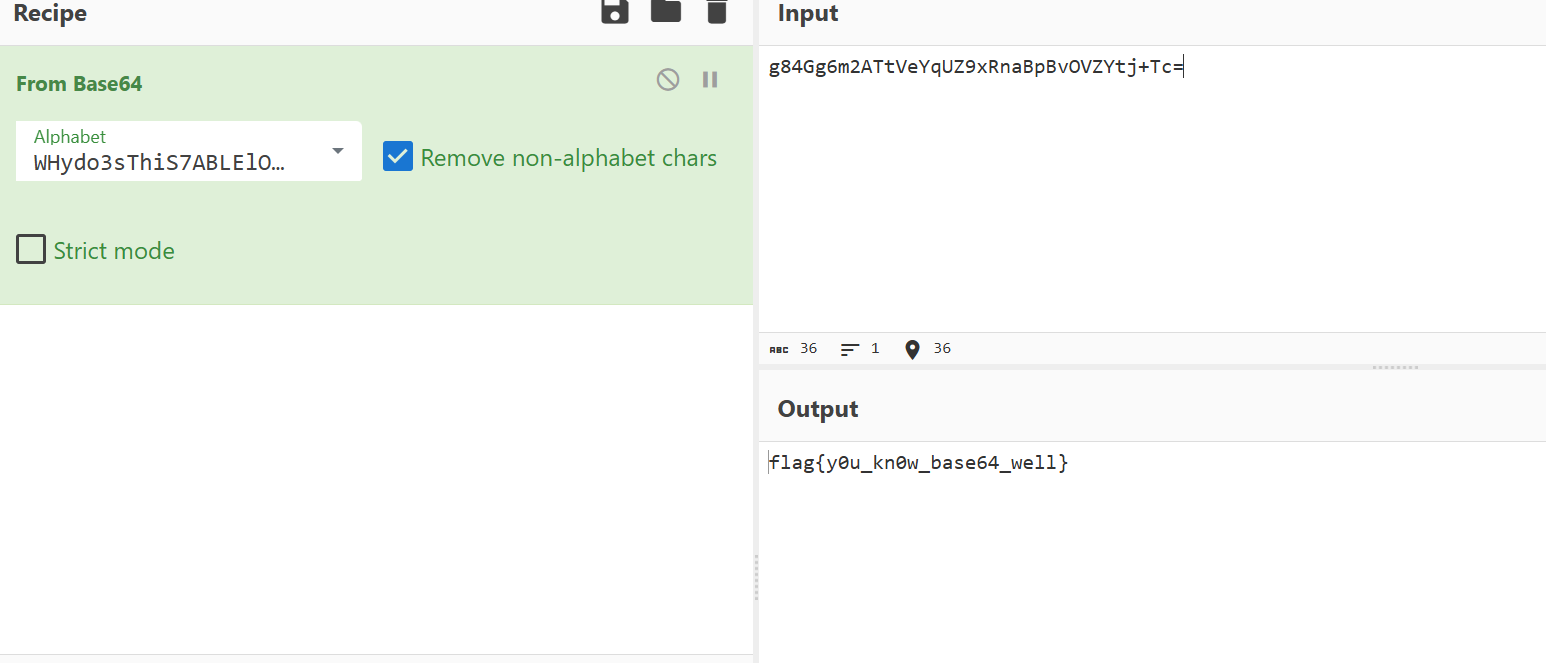
flag{y0u_kn0w_base64_well}
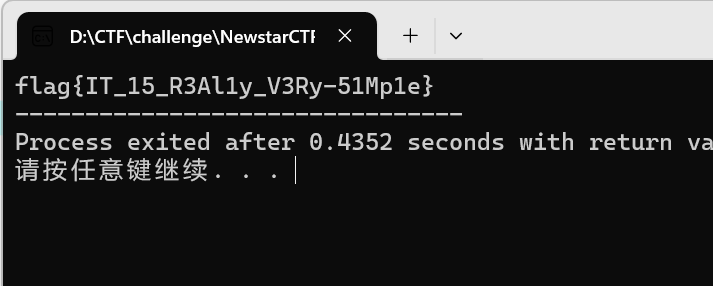
simple_encryption
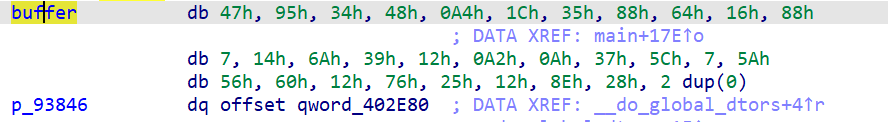
主函数逻辑为根据下标进行不同加密,逆向之即可
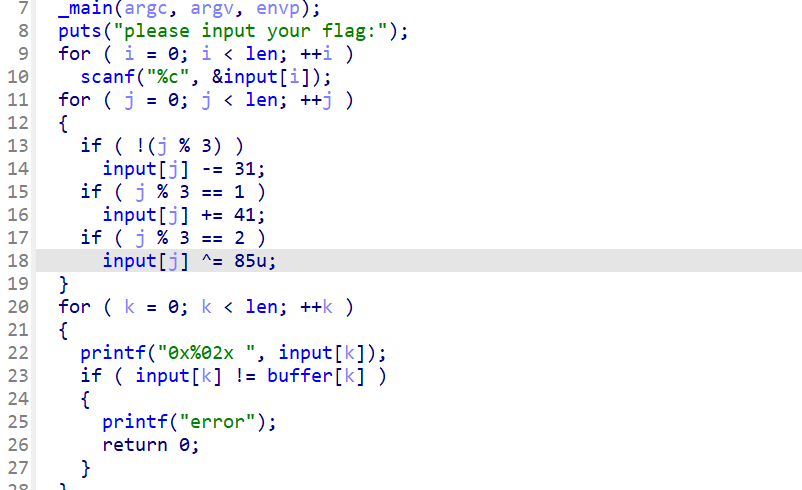
嘛
#include<stdio.h>
int main()
{
unsigned char buffer[32] = {
0x47, 0x95, 0x34, 0x48, 0xA4, 0x1C, 0x35, 0x88, 0x64, 0x16, 0x88, 0x07, 0x14, 0x6A, 0x39, 0x12,
0xA2, 0x0A, 0x37, 0x5C, 0x07, 0x5A, 0x56, 0x60, 0x12, 0x76, 0x25, 0x12, 0x8E, 0x28, 0x00, 0x00
};
for(int i=0;i<=31;i++)
{
if(!(i%3))
{
buffer[i]+=31;
}else if(i%3==1)
{
buffer[i]-=41;
}else if(i%3==2)
{
buffer[i]^=85;
}
printf("%c",buffer[i]);
}
return 0;
} 
ezAndroidStudy
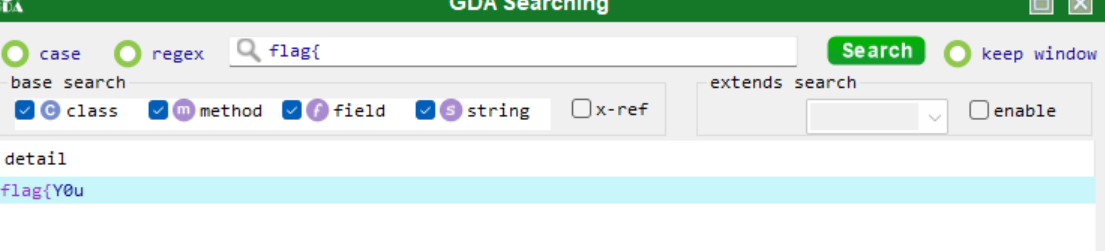
flag{Y0u
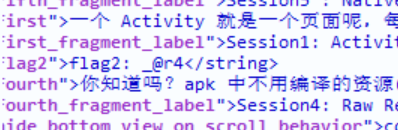
_@r4
 _900d
_900d
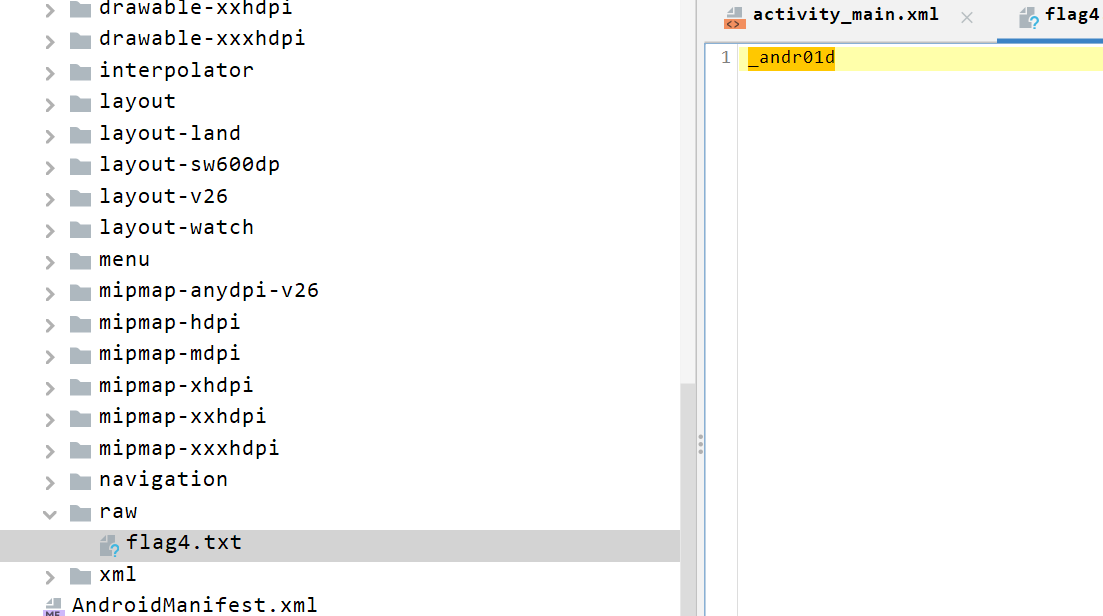
_andr01d
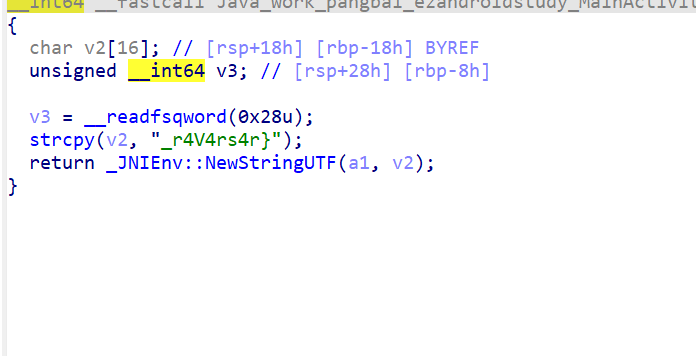
_r4V4rs4r}
flag{Y0u_@r4_900d_andr01d_r4V4rs4r}
ez_debug
x64dbg动调,随便输个假flag单步,在寄存器界面可发现输入的flag先与23异或再与ATRI对位异或,IDA分析界面可以看到与v2526比较,于是得到密文,逆向即可解出
#include<stdio.h>
int main()
{
int a;
a='1'^'&';
//printf("%d",a);
char enc[30]="0/$9-:u+\t\"7m\t$u12";
enc[17]='\x1c';
enc[18]='\x05';
enc[19]='\x01';
enc[20]='\x12';
enc[21]='&';
enc[22]=27;//'
enc[23]='+';
enc[24]='o';
enc[25]='>';
char key[5]="ATRI";
for(int i=0;i<=27;i++)
{
printf("%c",enc[i]^a^key[i%4]);
}
return 0;
} 这里有一位密文缺失手动补全了一下)
flag{y0u_ar3_g0od@Debu9}


